If I can selfhost an application (preferably open source) I’m probably going to do it. It gives you control over your data and might learn a few things while doing it.
Until now I spun up these tools and managed the users in each of them. Sharing a few of these applications makes managing users in each of them cumbersome, especially if people start forgetting passwords etc…
Having managed tools with LDAP professionally I wanted to set one up for myself.
LLDAP – Light Lightweight Directory Access Protocol
I started looking for open source tools and OpenLDAP and FreeIPA evidently popped first but also found LLDAP. Kinda only “production” ready since version 0.3 which was released Juli this year makes it a fairly new as well. Below a list of the points I was debating over if I should try it out or not. But quickly realized I’d probably don’t need a full fledged LDAP server so I went with it.
Pros:
- Light on resources
- RAM (less then 100MB under load)
- CPU
- Disk usage (<- a lot smaller then the competitors)
- Simple WebUI
Cons:
- Not full ldap implementation
Installation
Since I use Unraid, installing it is fairly simple as someone already made a template for it in the community app store using the official image. (docker hub)
If you’re just using docker you could do use a compose file like this:
version: '3'
services:
lldap:
hostname: LLDAP
image: nitnelave/lldap:stable
ports:
- "3890:3890"
- "17170:17170"
volumes:
- 'apathtolldapdata:/data'
- /data
environment:
- UID=1000
- GID=1000
- LLDAP_JWT_SECRET=<replace>
- LLDAP_LDAP_USER_PASS=<replace>
- LLDAP_LDAP_BASE_DN=dc=ziggyds,dc=beSearch for LLDAP and click Install
The next screen will show you all the parameters that need/can be passed on to the container.
Data path – will map everything that will be written to /data inside the container to your chosen location on the array or cache disk.
Make sure to pick a safe admin password and JWT secret.
Set your base dn, I just kept in simple and went with my domain.
The default LDAP-protocol port is 389 (LDAPS 636) but LLDAP defaults to 3890.
You can freely pick any available port but I went with 389 since it is the ldap default.

Click apply and Unraid will set up LLDAP via a docker run command.
It should only take a couple of seconds and once that is done you can browse to the Web-UI.
Default admin credentials are admin and the password is the one you set for LLDAP_LDAP_USER_PASS.
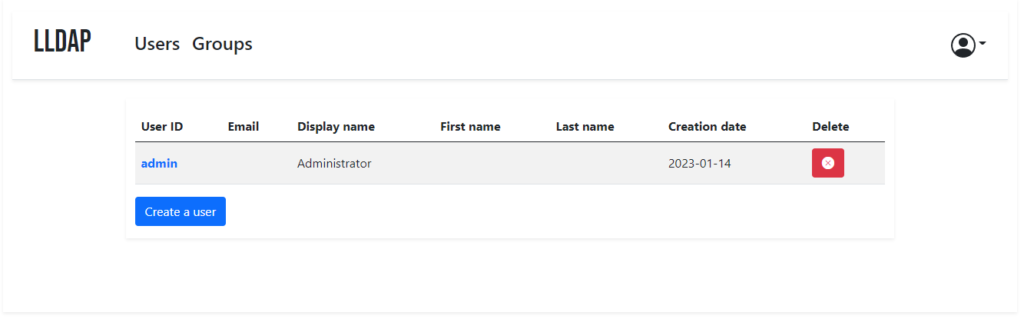
The Web-UI is pretty straight forward. You can create users and groups and you can put users in groups.
Rancher LLDAP configuration
Now LLDAP is setup it is time to link it to one of my tools.
In their git repository you can find a whole folder with config examples for different tools.
https://github.com/nitnelave/lldap/tree/main/example_configs
Additionally I’ll another one here for Rancher.
For this example I created a test user and a group in LLDAP.
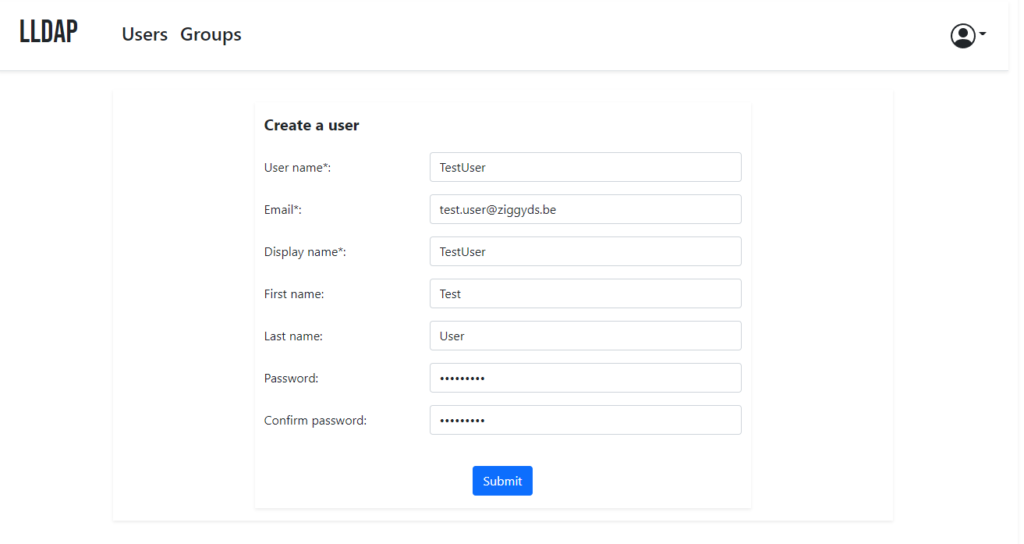

We’ve to add the user to the group of course by going to the user, selecting the Rancher group and click add.

Once that is done we can configure Rancher to check for users in this group.
In Rancher go to Configuration -> Users & Authentication.
Since there is no specific LLDAP or general LDAP option, I picked OpenLDAP.

In the end your config should look something like on the screenshot below.
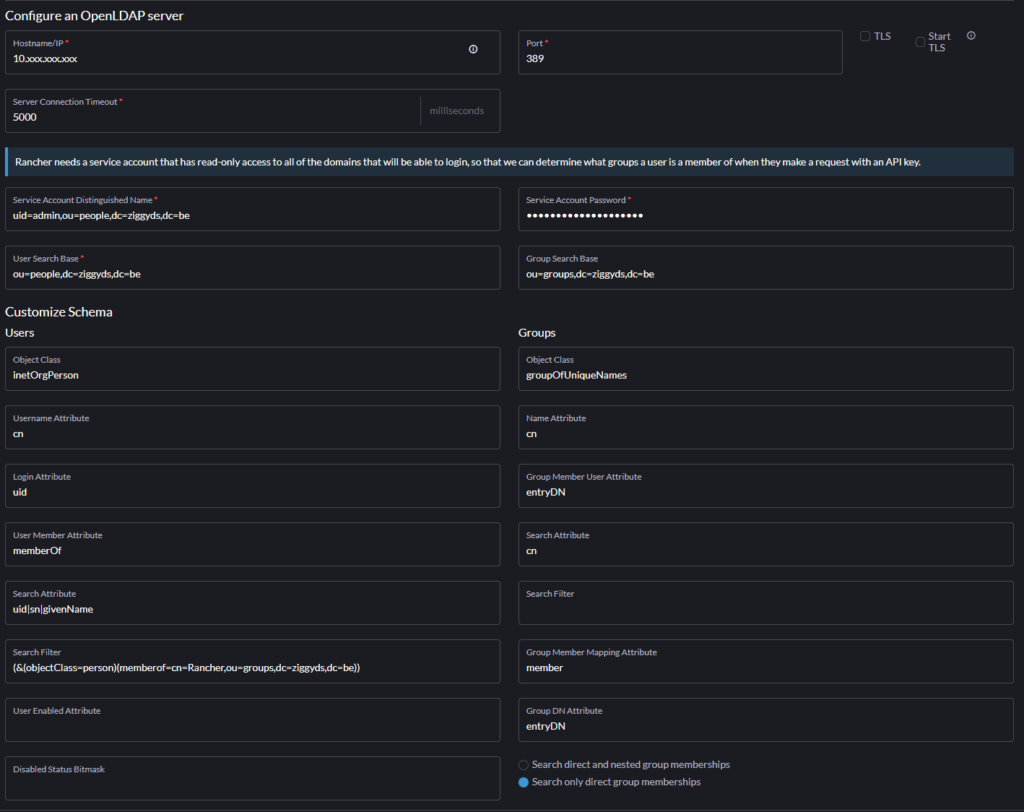
By default some fields are already filled in. Below I’ll highlight the ones I had to modify.
Server connection
Set the hostname and port of the LLDAP instance.
I used the admin user as service account but you could create a specific one for Rancher.
User and Group Search Base set to ou people and groups as this is were they are located.
Schema – Users – Search Filter
(&(objectClass=person)(memberof=cn=Rancher,ou=groups,dc=ziggyds,dc=be))This LDAP query specifies that the search should return only objects that have the “objectClass” attribute set to “person” and that they are a member of the Rancher group.
“&” denotes an “AND” operation, so both conditions must be met. It has to be a person logging in and he has to be a member of the Rancher group.
Schema – Groups – Object Class
Change groupOfNames to by the default in LLDAP present groupOfUniqueNames.
Saving Configuration
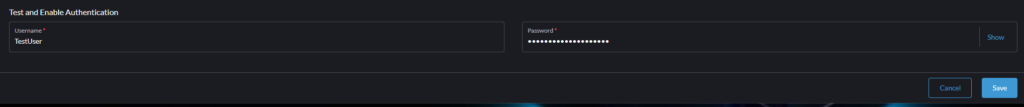
Before saving the config we’ve to fill an existing user that is part of Rancher group. Rancher will see if it get retrieve the details.
Once that is done Rancher will reflect that the OpenLDAP Authentication Provider is active.
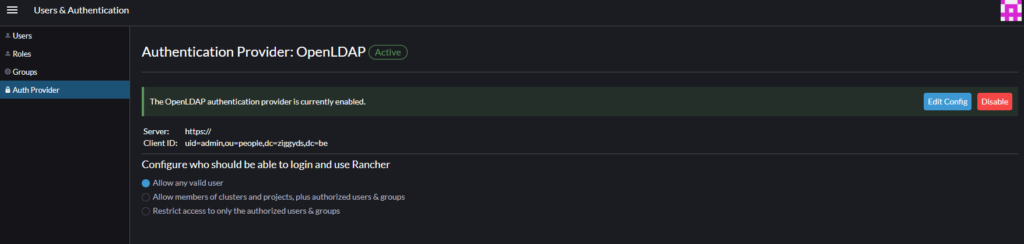
And you’ll notice you can now login using the users in your LLDAP users.

Comment